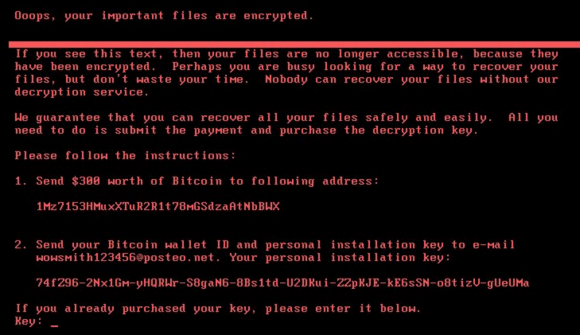
Just a month after the then-historic WannaCry ransomware cyber-attack went viral around the globe, another one dubbed "Petya" started hitting Europe early this morning, then spread to North America as the work day started and people switched on their computers on and logged in.
Many large European organizations have already confirmed being hit, including Ukraine's government and several of its largest banks, Danish shipping giant Maersk, major international law firm DLA Piper, and many more.
According to cyber-security software maker Webroot's blog post, Petya takes advantage of the same "Eternal Blue" security vulnerability in Microsoft Windows as WannaCry did. Microsoft released a patch (MS17-010) for the vulnerability in March of this year, but many companies put off installing the patch for a variety of reasons.
Petya also adds a few twists to make it even nastier - including the lack of a master kill switch, and the ability to search and find passwords on one computer, and then use them to access other PCs on the same network. Additionally, this time the cyber-attack appears to be the work of professionals, rather than the North Korean amateurs rumoured to be behind WannaCry.
 bout the latest trends and threats, and invest both time and money in the best techniques and tools available, all with the goal of keeping our clients' safe.
bout the latest trends and threats, and invest both time and money in the best techniques and tools available, all with the goal of keeping our clients' safe.
If you're not a Sentryon plan client, there are four things you should check immediately to ensure your critical business systems and data are protected:
- Keep network devices and computers fully patched and up-to-date. New vulnerabilities are frequently found in common software programs such as Microsoft Windows, Microsoft Office, Adobe Reader, and others. Therefore, it's critical to patch and update systems and applications when patches become available. The WannaCry ransomware in particular exploited a vulnerability in Windows systems that were missing a critical security patch released back in March.
- Replace Out-of-Date Software. As software vendors release new versions of their programs, they often cease support for older versions, which means no security updates or patches. If you continue using software that is no longer supported, you are placing yourself at a higher risk for security attacks.
- Install a Business-Grade "Image" Backup System BOTH On-Premise and In The Cloud. This important step can save the day with even the most aggressive (and new) ransomware attacks. Ransomware works by locking up your files and then demanding payment to restore access to them. But if your files are safely backed up, you don't need to worry about paying a crook to get them back.
- The #1 Security Threat To ANY Business Is.... YOU! Like it or not, almost all security breaches in business today are due to an employee clicking, downloading, or opening a file that's infected, either on a website or in an email. Encourage employees to follow this simple rule: DO NOT CLICK on links or attachments from unknown senders - PERIOD.
This is not an exhaustive list though, and there are many more security layers that need to be in place to fully protect your company from existing and newly emerging security threats.
If you know another business leader who is concerned that their systems are not as well protected as they would like, and would be interested in a complimentary 68-Point IT Security & Performance Assessment, please call us at 416-440-1400 or send us a message.

You must be logged in to post a comment.