Email phishing (pronounced "fishing") attacks aren't new, but the con-artists and criminals behind them are always innovating to find new and better ways to sucker people into becoming victims. And because it's national Cybercrime month, we thought it was a good time for a refresher on one of the most common attack vectors for businesses.
Just for a bit of background, a phishing email is one that looks like a legitimate message from a client, vendor, supplier, service provider, or even from within your own organization, but which in actual fact is from someone else with ulterior motives. There are a few objectives these emails have:
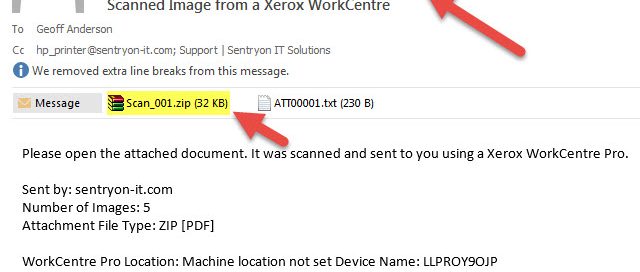
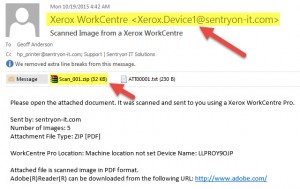
- Getting you to open a .zip file attachment and run an .exe file inside which installs malware on your computer, which can then be used to steal your information, monitor your keystrokes, or any number of other nefarious things.
- Get you to click a link which goes to a rogue website that looks legitimate (e.g. your bank, credit card company, email provider, etc.) and enter your credentials, which they then steal and use to log into the real website.
- And more recently we've seen emails containing .html attachments (stand-alone web pages) which look like a Gmail login page asking for your email address and password. If you are conned and provide this, your real Gmail account will then be compromised and used to send emails to everyone in your list.
The picture below is one we received recently which appears to be from a Xerox copier inside our company. Now, we don't have any Xerox equipment here, so it's easy to know this is a fake. But if your company does and you got something like this, you might be fooled into believing it's real. The big clue here is the kind of attachment - copiers never send .zip files (compressed archives containing one or more other files), only image files like .pdf, .jpg or .tif, all of which are relatively safe.
The best way to avoid becoming a victim of phishing is to keep your guard up, be careful and only open attachments from senders you know and were expecting (if in doubt, call them and ask). You should also have a good commercial security software like Symantec, Kaspersky, Webroot or similar, and make sure it's kept current. A good anti-spam filtering service can also help eliminate receiving these messages in the first place.
If you do happen to get a phishing email, don't click any links or open attachments just to see what's inside them - delete the email right away and let your IT provider know immediately.
Sentryon IT Solutions

You must be logged in to post a comment.